
Introducing Consequence-Driven, Cyber-Informed Engineering (CCE)
- We are fighting a losing battle
“Every year while we may be improving slightly, the gap between attacker and defender capabilities is widening. The folly of continuing down the same well-trodden incremental improvement path we’ve constructed over the past few decades is now plain for all to see. More and more money spent on new cybersecurity products and services, with hard-to-measure but-low-percentage-of risk “transferred” via the emerging cybersecurity insurance market. Sadly, insurance isn’t the escape hatch it seemed it might become.
Those who’ve been in the fight for a few years will find CCE a compelling resource to share with their mentees. But for the far too many who still turn to hope and hygiene to address these challenges, the perspective will serve as a cold dash of reality.” QUOTE: Bochman, Andrew A.; Freeman, Sarah. Countering Cyber Sabotage. Taylor and Francis.
- Idaho National Laboratory (INL) evolved CCE to answer the challenge
As opposed to looking through the classic cyber defense lens INL decided to assume the worst and look backwards from consequences. This process they then refined into four phases:
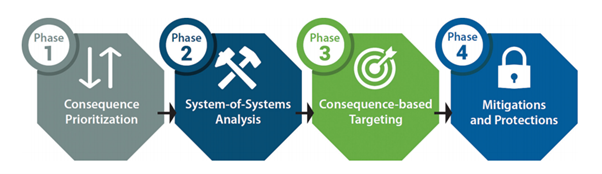
Observer Solutions are proud to partner with INL to help our clients gain essential insights through a series of high impact review sessions or (for the more committed) achieve CCE Enabled Status® .
Accepting that it is not a matter of IF more of WHEN you will experience a breach, CCE surfaces the practical steps you should take post breach. Then you are informed and can tackle the question of how often, with what level of detail simulated breaches are run and who needs to be involved.
“All of this is under our control. Cyber is not an Act of God” QUOTE: Curtis St. Michel, CTO, INL Cybercore Integration Center
